In today’s interconnected world, managing network devices efficiently is essential for maintaining seamless connectivity and security. Whether you’re a network administrator or an IT enthusiast, having a reliable and straightforward way to access your MikroTik devices is crucial. That’s where Winbox login emerges as a powerful tool — offering a user-friendly interface to configure and monitor MikroTik routers and switches effectively. This comprehensive guide explores everything you need to know about Winbox login, from initial setup to advanced management techniques, ensuring you maximize your network’s potential.
Understanding the Significance of Winbox Login in Network Management
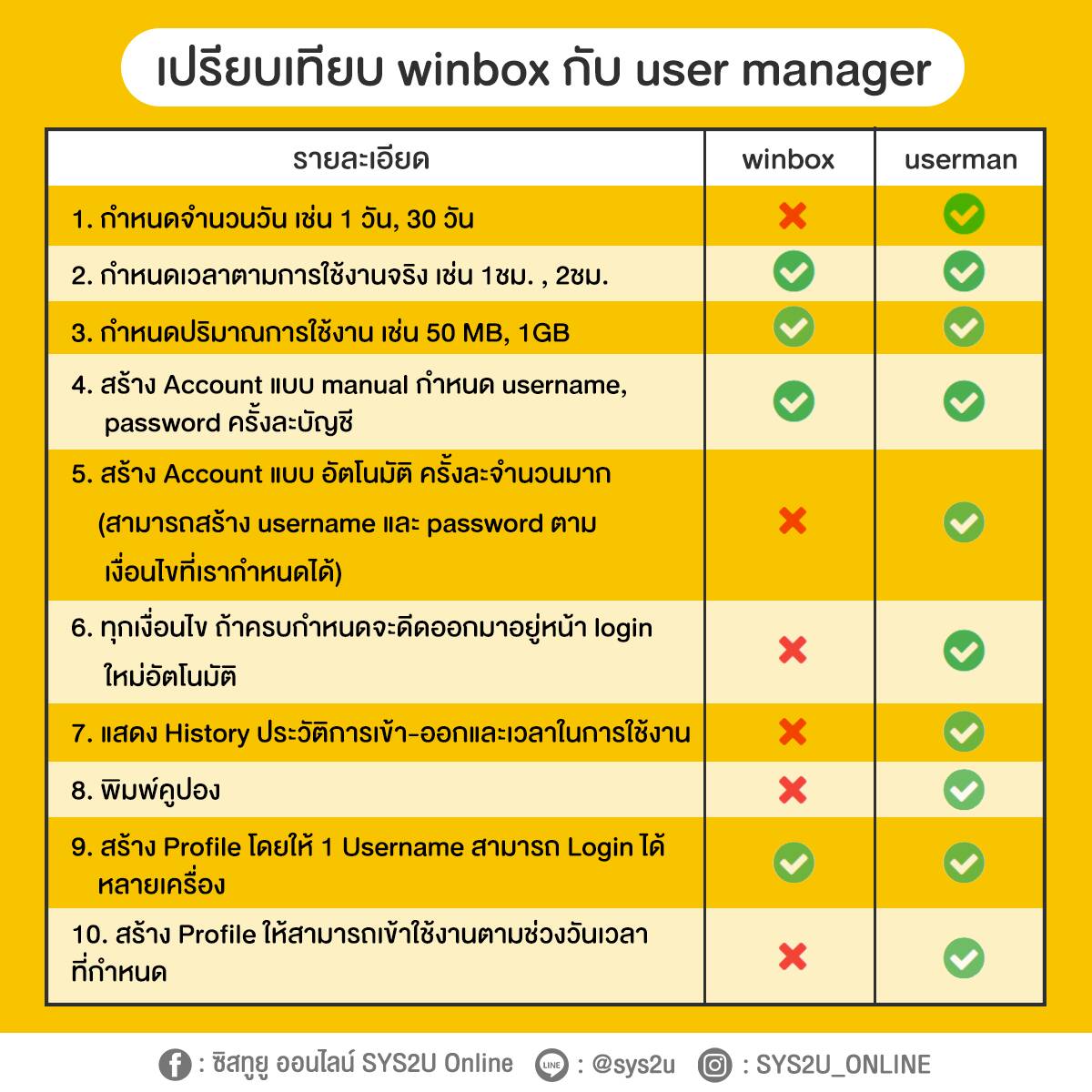
Mastering the Winbox login process is fundamental for anyone involved in network management that leverages MikroTik hardware. The tool integrates simplicity with advanced functionality, giving administrators an intuitive interface directly connected to their network devices. Without this direct access method, managing MikroTik routers becomes complicated and time-consuming, especially when dealing with complex configurations, updates, or troubleshooting.
The importance of Winbox login extends beyond mere accessibility. It provides a secure and flexible way to perform configurations, monitor system status, and execute commands efficiently. As the backbone of network control, Winbox facilitates rapid adjustments, ensuring minimal downtime and optimal network performance. Moreover, it bridges users with MikroTik’s powerful RouterOS, enabling features and functionalities that might otherwise require more complex command-line operations.
A common misconception is that Winbox login is only for seasoned professionals. However, its user-friendly interface simplifies operations for beginners while maintaining the robustness required by seasoned network engineers. This duality emphasizes why understanding and mastering Winbox login is a strategic advantage for anyone managing MikroTik-based networks.
Setting Up Your Winbox Login Environment – Preparations and Essentials

Before diving into the actual Winbox login, you need to ensure your environment is correctly prepared. This phase involves verifying network connectivity, configuring your MikroTik device for remote access, and acquiring the latest Winbox software. Proper preparation makes the login process smooth and minimizes potential security issues.
To successfully log in using Winbox, you must connect your computer to the network where the MikroTik device resides. This connection can be established via Ethernet or over Wi-Fi, provided the device’s default or configured IP address is accessible. Ensuring that your device’s IP is in the same subnet as your computer is critical for an uncomplicated initial connection.
Another essential step involves configuring your MikroTik device to accept Winbox login requests. This action includes enabling the Winbox service if it isn’t already active and ensuring that firewall rules permit your IP address to access the device’s management port, typically 8291. You should also verify that your user credentials are correctly configured, with strong passwords to enhance security.
Finally, download the latest version of Winbox from MikroTik’s official website. The application is lightweight and portable, allowing you to carry it on a USB drive or download it directly on your management workstation. Keeping your Winbox version updated ensures compatibility with the latest RouterOS features and security patches, which is vital for maintaining a safe management environment.
Step-by-Step Guide to Accessing Your MikroTik Device with Winbox Login

Once your environment is ready, accessing your MikroTik device through Winbox login becomes a straightforward process. This operation involves launching the Winbox application, discovering your device, and securely entering your credentials. Here’s a detailed walkthrough to simplify this vital step.
Start by opening the Winbox application on your management workstation. When the software launches, you will notice two primary methods to connect: via MAC address or IP address. If you are on the same local network and don’t have IP connectivity issues, you can select the MAC address for a direct, no-IP configuration. For remote connections or devices with dynamic IPs, use the IP address option.
To discover your device, click the “Neighbors” button, which scans the network for MikroTik devices on the local subnet. If your device appears in the list, select it. Otherwise, manually enter the router’s IP address in the appropriate field. Translating this into real-world practice, it’s often helpful to assign static IPs to your network devices or reserve DHCP addresses to simplify management.
Next, input the username and password credentials you set during initial setup or as per your security policy. For first-time login, use the default username ‘admin’ with no password or the credentials configured during setup, then change them immediately to prevent unauthorized access. Press “Connect,” and if all gateway information is correct, the connection will establish, granting you access to the MikroTik device’s graphical interface.
Once connected, the Winbox window will populate, displaying device details, system status, and menu options. From here, network professionals can perform configurations, manage interfaces, set up routing, firewall rules, and more, all through the intuitively designed GUI that simplifies what would otherwise be complex command-line processes.
Enhancing Security and Troubleshooting Winbox Login Issues
Security is a core concern when managing network devices, especially when remote access tools like Winbox login are involved. Ensuring the security of your login credentials and managing access properly helps prevent unauthorized control over your network. Equally important is troubleshooting common Winbox login issues to maintain consistent access and control.
Many users encounter problems during Winbox login, often related to misconfigured firewall rules, network issues, or outdated software. Identifying the root cause involves a systematic approach: verify network connectivity, confirm IP and port accessibility, and check user credentials. If the router isn’t responding, performing basic ping tests to the device’s IP address can help diagnose connectivity problems.
Firewall settings on both the MikroTik device and your management station can block Winbox traffic, especially if security policies are tightened. Ensure that port 8291 for Winbox is open in the device’s firewall rules, and your management station’s firewall allows outbound traffic on this port. Using tools like Telnet or Netcat can help verify if the port is accessible from your device.
When facing persistent login issues, consider resetting the device’s configuration, especially if credentials have been lost or misconfigured. MikroTik provides a safe reset method that preserves data, allowing you to restore default credentials and settings. Additionally, updating RouterOS and Winbox software ensures compatibility and patches potential security vulnerabilities.
Security best practices include disabling Winbox access when not needed, using strong passwords, and employing VPNs for remote management. These steps reduce the attack surface, protecting critical network infrastructure. Regular backups of configuration files further safeguard against accidental misconfigurations or hardware failures, enabling swift recovery.
Advanced Management: Automating & Optimizing Winbox Login for Enterprise Networks
As professional networks grow increasingly complex, automation and optimization of Winbox login and management activities become imperative. Moving beyond manual login processes, network administrators can leverage scripting, API integrations, and remote management tools to streamline operations, improve security, and ensure high availability.
Automation begins with scripting APIs or command-line tools compatible with RouterOS, such as scripting within Winbox or using external management platforms. These methods facilitate scheduled configurations, batch updates, and remote troubleshooting without requiring manual login each time. For enterprises managing multiple MikroTik devices, centralized management platforms or Network Management Systems (NMS) integrate with Winbox-compatible APIs.
Another essential consideration involves VPN and secure tunnels. By establishing VPN connections to your network, you centralize access, reduce exposure of management ports, and enhance security. Utilizing secure tunnels ensures that Winbox login sessions happen over encrypted channels, reducing the risk of interception or unauthorized access.
Monitoring tools and dashboards also enhance management efficiency. Integrating SNMP, Syslog servers, and network performance monitors with MikroTik devices allows real-time insights and automated alerts. These tools can include scripted actions triggered by specific events or thresholds, enabling proactive management rather than reactive troubleshooting. They effectively turn Winbox login from a manual task into part of an intelligent, automated network management ecosystem.
To finalize, adopting best practices in device management includes regular firmware updates, establishing role-based access controls, and employing multi-factor authentication where supported. These strategies not only safeguard against breaches but also optimize the overall management workflow, making Winbox login a secure and efficient process for enterprise environments.
Conclusion
Mastering Winbox login is a vital step toward efficient and secure network management with MikroTik devices. From initial setup and configuration to troubleshooting and advanced automation, understanding this process unlocks many capabilities that enhance network performance and security. As networks expand, employing best practices—including secure access methods, regular updates, and automation—becomes increasingly important for maintaining operational integrity. Whether you’re managing a small office network or large-scale enterprise infrastructure, proficient use of Winbox login empowers you to keep your network running smoothly, securely, and with maximum flexibility.